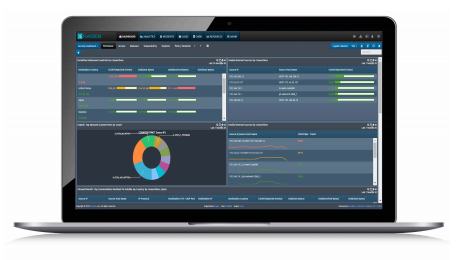
Fortinet User and Entity Behavior Analytics (UEBA)
Detect and prevent insider threat with user and entity behavior analytics (UEBA)
Features and Benefits
![]()
Hardware Assisted Encryption
Prevent breaches and secure data in transit at a very high speed.
![]()
Scalable Security
Scalable security that is seamlessly integrated with routing.
![]()
Comprehensive Data Communications Security
Protects Application to Application, User to Users, User to Machine, Machine to Machine communication.
![]()
Diverse VPNs
IPsec or SSL based diverse VPNs to offer flexible secure network choices.
![]()
Secuirty Fabric Integration
Share FortiTelemetry information across site-to-site tunnels with required confidentiality.
![]()
Unified Management
Simplified, easy-to-manage, single pane of glass to manage large scale crypto VPNs, Routing and NGFW.