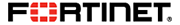
Fortinet Public Cloud Security
Secure Your Public Cloud Infrastructure and Workloads
Gain Visibility and Control Over Your Cloud Environments and Applications
Organizations are increasingly deploying a variety of workloads across multiple clouds. In turn, business-critical data and services are increasingly scattered across this distributed infrastructure. Using the shared responsibility model as a guiding principle, enterprises rely on cloud providers to protect the network, storage, and computing layers, while enterprises own the security for everything that is built, deployed, or stored in the public cloud. Due to multi-cloud adoption, most enterprises maintain heterogeneous environments, with tools from each cloud platform differing significantly.
Fortinet Cloud Security Solution Functions and Products
Fortinet adaptive cloud security solutions and products complement the power and scalability of cloud providers by breaking down the barriers that complicate security visibility and management across an organization’s entire infrastructure. At the same time, Fortinet streamlines operations, policy management, and visibility for improved security lifecycle management with full automation capabilities. And with native integration of security capabilities to each cloud platform, Fortinet products enable broad protection of applications and support for the broadest set of cloud use cases.
The Fortinet network security product line is available on all of the leading cloud providers with BYOL or on-demand per-usage (PAYG) options.
Management and Automation
- FortiManager: Cloud-based management for Fortinet products
- FortiAnalyzer: Cloud-based reporting to streamline SOC operations.
- FortiSIEM: Fortinet's multi-vendor Security Information and Event Management solution.
- FortiCWP: A security broker controls and monitors the organization's management of public cloud infrastructures.
Broad Protection
- FortiGate: Industry leading next-generation firewall runs in the cloud or on-premise
- FortiWeb: Fortinet's web-application firewall protects web applications and helps with patching and regulatory compliance.
- FortiMail: Secure email gateway protects against email-bourne threats and data loss via email.
- FortiSandbox: Offers a powerful combination of advanced detection, automated mitigation, actionable insight, and flexible deployment to stop targeted attacks and subsequent data loss.
Native Integration
- Fortinet Cloud Connectors: Provide an abstraction layer for Fortinet products to treat cloud infrastructures in a seamless manner by translating. Network addresses into security objects and providing various other security integrations with cloud provider API’s.
- Fortinet Fabric APIs: The APIs enable automated operations through dynamic sharing of local and global threat intelligence across security components.
- Fortinet DevOps stiches: Automation recipes making security or infrastructure events automatically trigger actions.
Available in:
Fortinet offers its industry leading series of network security products over the Oracle Cloud enabling you advanced security protection for your cloud based infrastructure and applications.
![]()
Amazon Web Services (AWS)
- FortiGate Next-Generation Firewall
- FortiWeb Web Application Firewall (WAF)
- FortiManager (BYOL) Centralized Security Management
- FortiAnalyzer Centralized Log Analytics
- FortiMail-VM BYOL
- FortiSandbox Advanced Threat Protection
![]()
Microsoft Azure
- FortiGate Next-Generation Firewall (NGFW) - Single VM
- FortiWeb Web Application Firewall
- Fortinet FortiSandbox Advanced Threat Protection
- FortiMail Secure Cloud Email
- FortiManager Centralized Security Management
- FortiAnalyzer Centralized Log Analytics
![]()
Google Cloud Platform (GCP)
- FortiGate Next-Generation Firewall
- FortiWeb Web Application Firewall
- FortiManager Centralized Security Management
- FortiAnalyzer Centralized Log Analytics
![]()
Oracle Cloud (OCI)
- FortiGate Next-Generation Firewall for OCI
- FortiWeb Web Application Firewall
- FortiManager Centralized Security Management
- FortiAnalyzer Centralized Log Analytics
![]()
Alibaba Cloud
- FortiGate Next-Generation Firewall - Single VM (On-Demand)
- FortiGate Next-Generation Firewall - Single VM (BYOL)
- FortiManager Centralized Security Management
- FortiAnalyzer Centralized Log Analytics
FortiGate Cloud Firewall Ecosystem

Public Cloud Security Use Cases:
Security in the cloud is intended to increase the organizations confidence to deploy applications in the cloud and by such improve overall organizational agility and ability to respond to market demand. By leveraging Fortinet’s Security Fabric solutions to deploy use case driven security capabilities, organizations benefit from market leading security with streamlined management functionality. Following is a set of common deployment scenarios of Fortinet’s Security Fabric:
Platform Security:
SaaS Visibility and Control
Software-as-a-Service (SaaS) application usage is often unregulated and unsecure. A lack of visibility and control on SaaS applications usage heightens risk.
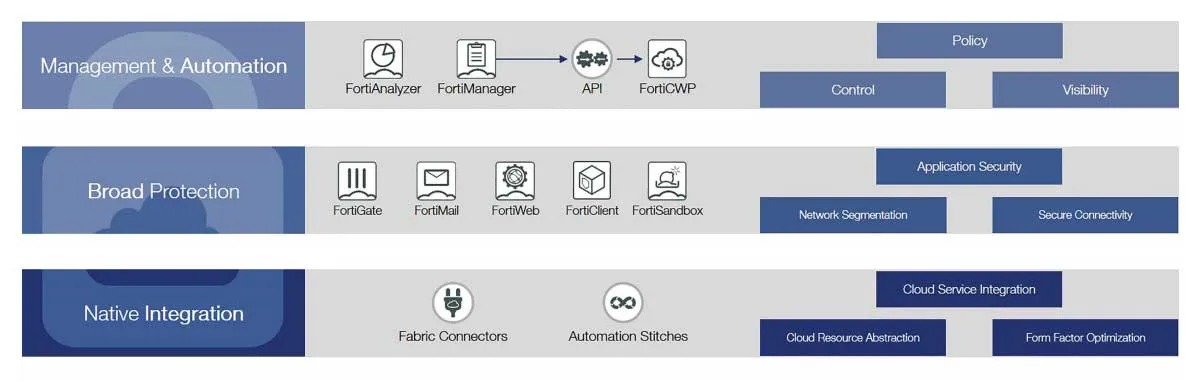
Solution
FortiCASB-SaaS leverages the SaaS application API to monitor all SaaS activity and configuration of multiple SaaS services.
FortiCASB-SaaS provides centralized, detailed visibility on all SaaS applications usage. This enables organizations to implement uniform application control and security policies, protect their sensitive data against advanced threats, and support security compliance and governance.
Benefits
- Organizations gain full visibility over usage of SaaS applications including their potential to spread malware or leak data
- Provides full support for major SaaS applications such as Salesforce.com, Microsoft Office 365, etc.
Cloud Infrastructure Visibility and Control
As cloud use increases, so does the likelihood of misconfiguration. Analysts estimate that by 2023, misconfiguration will cause 99% of cloud-related risk, leading to disrupted services and unexpected costs.
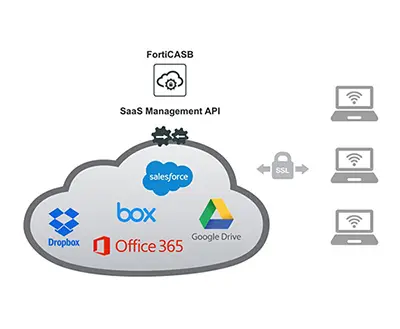
Solution
FortiCWP leverages the public cloud management API to monitor activity and configuration of multiple cloud resources. It continuously evaluates configurations across regions and public cloud types, and provides consistent visibility. The solution simplifies regulatory compliance violation reporting, and enhances compliance by providing guidance on security best practices. It also offers threat and risk management tools that help trace misconfigurations to their source.
Benefits
- Consistent compliance reporting across multiple clouds
- Dynamic cloud heat map and threat maps
- Streamlined incident investigation
Compliance in the Cloud
For many organizations, it is a time consuming burden to achieve compliance with PCI DSS, HIPPA, SOX, GDPR, and other regulation mandates.
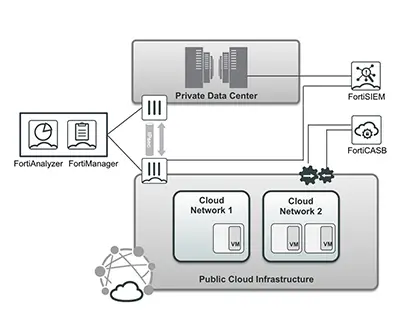
Solution
FortiCWP aggregates and organizes security information from multiple cloud services and API’s into meaningful compliance reports and live compliance dashboards.
FortiSIEM provides a broader view of compliance across multiple clouds, Fortinet Security Fabric products and third-party products. It can create compliance reports at the push of a button.
FortiAnalyzer collects logs from Fortinet Security Fabric elements, and FortiManager enables changes to be audited, reviewed, approved, and implemented. Together, they close the loop on compliance gap mitigation. All systems support automated processes to facilitate compliance policy management and workflow, reducing risk when policies are changed.
Benefits
- Automated compliance auditing and reporting for on-premises and cloud environments.
Cloud Based Security Management and Analytics
Using legacy management tools alongside new technologies creates complex incompatibilities, especially when seeking to manage from the cloud.
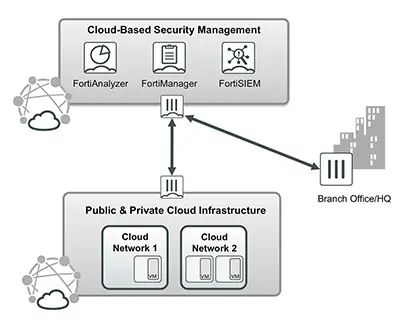
Solution
Leverage the multi-regional and global presence of top cloud infrastructure providers to deploy centralized and global security management and analytics systems in the cloud. FortiManager-VM, FortiAnalyzer-VM, and FortiSIEM-VM can all be deployed in the cloud to scale and globalize.
Benefits
- Centralized, unified security management and visibility
- Enhanced audit and compliance reporting
- Faster incident response
- Improved operational and cost efficiency, reducing risk
- Increased ability to automate security management
Application Security:
Web Application Security
Commonly cloud-based applications are using web services to communicate internally as well as outwards. Such applications are vulnerable to various threats and the organizations operating these applications are often required to meet compliance requirements.
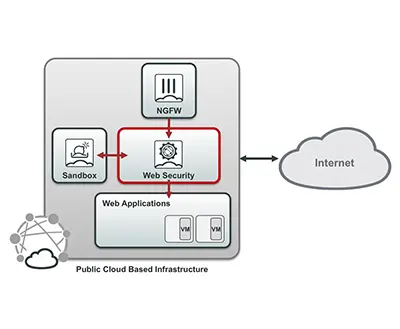
Solution
Fortinet offers a variety of web application security solutions that are ideally suited for cloud-based customers. FortiWeb-VM, a purpose-built industry-leading web application firewall offered on all major cloud platforms, secures web services application programming interfaces (APIs), as well as front-end web applications to protect from known and unknown threats. Through integration with FortiWeb, FortiGate-VMs centrally enforce security policies and provide increased visibility. FortiCloud Sandbox Service performs dynamic analysis to identify previously unknown malware.
Benefits
- Provide centralized protection for web applications
- Enhance regulatory compliance for applications
- Deploy API-specific security packages
- Automate threat responses with the Fortinet Security Fabric: FortiWeb detects threats and FortiGate blocks them
Container Security
Teams need to be able to rapidly develop modular applications in containers, whether on-premises, in the cloud, or within an orchestration tool such as Kubernetes. In addition, each application needs consistent protection against threats.
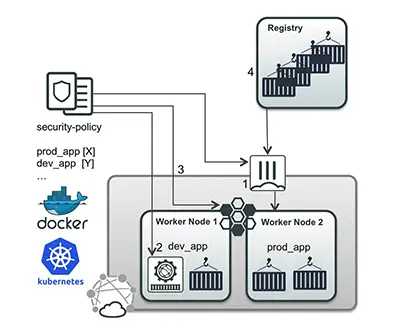
Solution
Fortinet’s container security solution is divided to four complementary areas of protection. Container-aware security with the FortiGate cloud connector enables awareness of container labels when defining security policies. Container-enabled security with FortiWeb as a container image can be bundled within an application chain. Container-integrated security allows a Fortinet solution to be dynamically integrated into Kubernetes clusters and inserted in the application chain. Container registry security with FortiSandbox scans pulled, pre-configured container images for zero-day threats.
Benefits
- Enable security for all stages of container deployment and rollout
- Support faster development with security elements built-in
Secure Productivity
As organizations increasingly outsource the IT management aspect of productivity and email applications, the visibility and control over these applications is reduced. Security teams need the ability to provide consistent purpose-built security across multi-cloud environments.
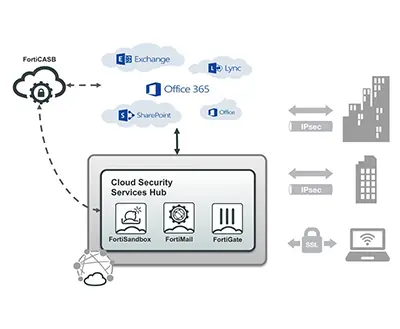
Solution
The combination of FortiMail, FortiSandbox, and FortiCASB-SaaS provides critical capabilities when securing Microsoft Office 365. The Fortinet Security Fabric enables deep visibility into email for protection from zero-day threats and monitoring the Office 365 application programming interface (API) layer.
Benefits
- Consistent on cloud / off cloud security
- Strong authentication, email security and cloud visibility
Network Security:
Secure Hybrid Cloud
Security posture is often inconsistent between data centers and clouds, leading to poor network visibility and complex security management. Connectivity needs to be protected between cloud environments and data centers.
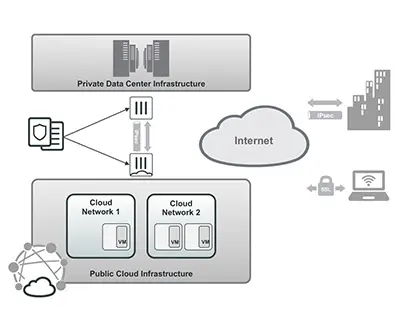
Solution
FortiGate next-generation firewall (NGFW) and cloud security solutions offer best-of-breed secure connectivity, network segmentation, and application security for hybrid-cloud-based deployments. They provide centralized, consistent security policy enforcement and connect through a high-speed VPN tunnel. FortiGate-VMs deployed in the public cloud can securely communicate and share consistent policies with FortiGate NGFWs of any form factor provisioned in a private data center.
Benefits
- High-speed virtual private network (VPN) connections protect data without compromising performance
- Security policies enforced consistently across all environments
- Single-pane-of-glass management
Cloud Security Services Hub
When teams develop applications in separate virtual networks and clouds, there is no centralized security management, making it challenging to secure the resulting applications and separate environments.
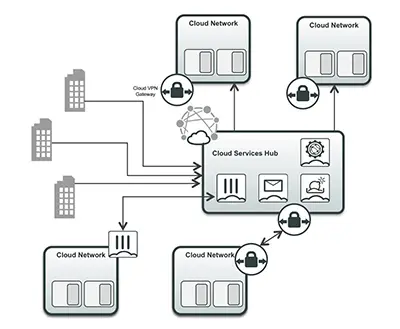
Solution
Security teams looking to unify disparate environments need a central security services hub, or transit network. The hub splits security from application development to provide centralized, shared, and consistent security enforcement. It also securely connects networks, locations, clouds, and data centers. Additionally, it analyzes and enforces security polices on inbound and outbound traffic between cloud and the internet.
Benefits
- Security enforced consistently across all networks
- Secure connections enforced between locations
- Teams can develop security solutions autonomously without waiting for security policies to be applied, reducing risk
Logical (Intent-Based) Segmentation
Segmenting cloud environments is challenging because dynamic provisioning results in constantly changing IP addresses. Network segmentation based on static IP address rules is therefore ineffective.
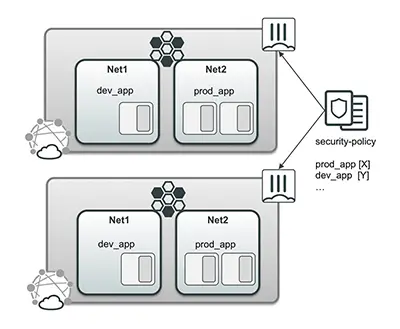
Solution
FortiGate-VMs provide intent-based segmentation, which builds access rules and segments based on user identity or business logic, and adjusts rules dynamically in response to a continuous trust assessment. FortiGate-VMs leverage metadata or tags associated with cloud-based resources across multiple clouds as an element in enforcing security policies. As a result, they intuitively define which workloads and elements in the cloud are allowed to communicate with other workloads and elements, whether they are inside or outside the cloud.
Benefits
- Able to dynamically adjust security policies based on logical roles of resources, accommodating the fluidity of changes
- Effectively blocks lateral attack movement and is able to inspect north-south and east-west traffic
Secure Remote Access
Organizations need global, on-demand, secure access to cloud resources. Traditional remote access VPNs, however, cannot meet these requirements.
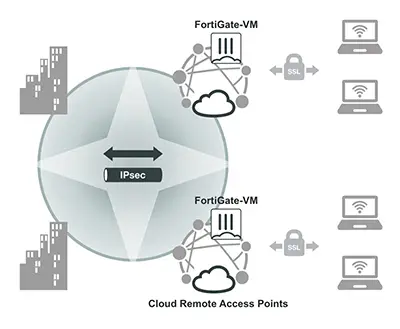
Solution
Security teams need configuration templates that enable secure remote access termination in the cloud. Then, they can dynamically provision FortiGate-VM instances that are pre-configured with these templates globally. This enables mobile workforces, customers, and business partners to connect to the virtual organization network. It also connects the cloud network to business applications through VPN tunnels, whether deployed in the cloud or on-premises.
Benefits
- Low-latency, always-on connectivity to business applications through closest entry point into the network
- Consistent user experience regardless of application location
- Global high availability design eliminates impact of network single point of failure
Features and Benefits
![]()
Streamlined and Automated Management
![]()
Consistent Security Across Public and Private Cloud Applications
![]()
Multi-Layer Advanced Application Protection
![]()
Flexible pay as you go billing and licensing
![]()
Scalable and resilient protection for elastic workloads
![]()
Support leading IaaS Provders
Deploy Any Application In Any Cloud With Fortinet
As the leader in multi-cloud security, Fortinet gives you the confidence to deploy any application in any cloud. Our solutions provide broad protection across the entire digital attack surface, both on-premises and in public clouds. Native integration with each of the major cloud providers enables automated, centralized management across all clouds uniformly and seamlessly. Giving you unified visibility and control and policy management that supports risk management and compliance requirements.
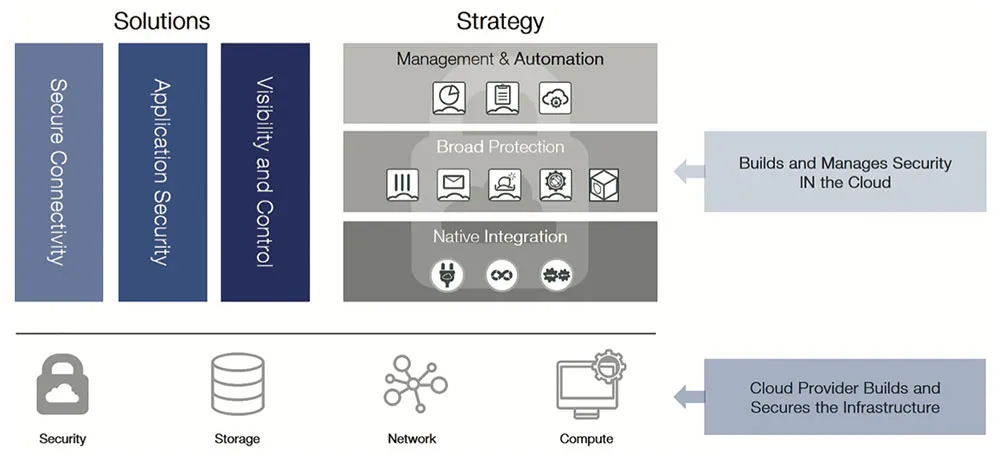
Fortinet cloud security addresses customer components such as your data and applications, operating systems, access and identity management, encryption, APIs, and network traffic. This complements the public cloud provider’s security features to provide complete and compliant protection.
Native Integration with Your Cloud Provider
Fortinet’s cloud security solutions and products enable secure workloads through tight integration with all major public cloud providers to ensure privacy and confidentiality while leveraging the benefits of scalability, metering, and time to market.
Our purpose-built cloud security solutions collaborate with key Fortinet products for varying cloud deployment models and use cases, while allowing for centralized management, open API integrations, metering consumption, cloud platform orchestration, and automation.

