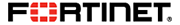Overview
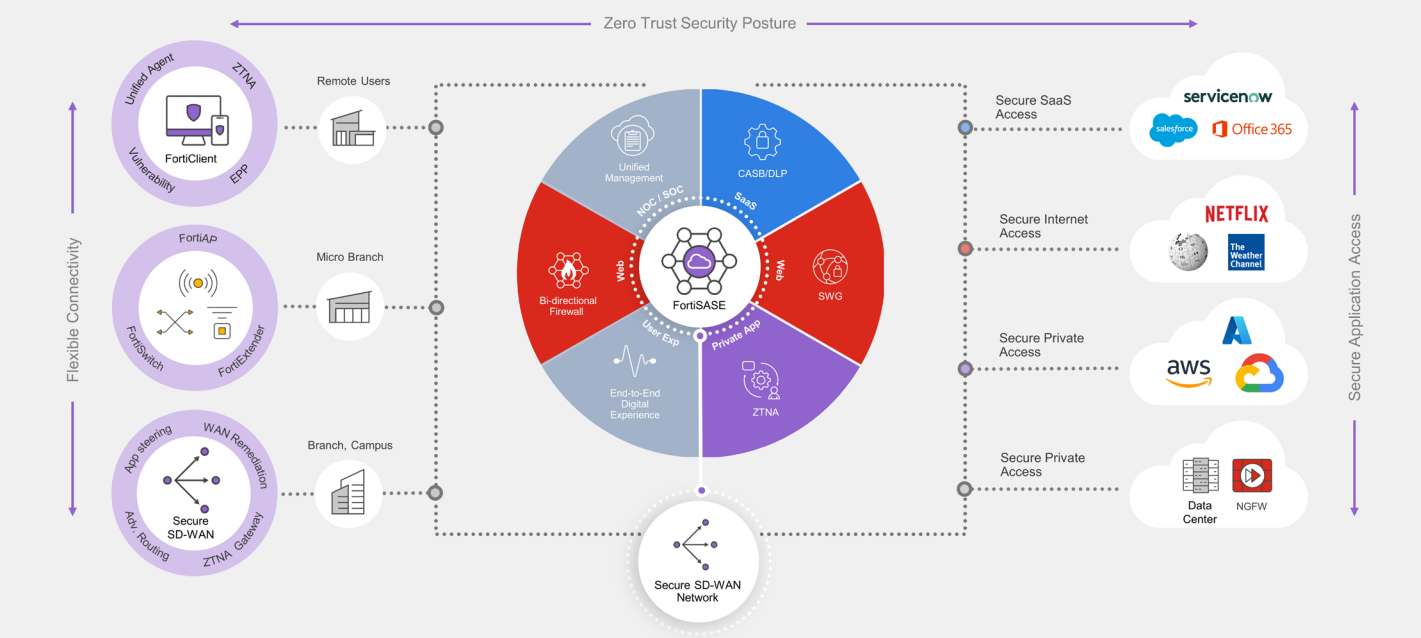
Universal SASE is a comprehensive Cloud-centric SASE solution to secure the hybrid workforce with the same underlying OS, AI-powered services, unified agent, management and experience monitoring. Universal SASE secures all users, devices and edges, including micro-branches for the best flexibility for organizations, with disparate architectures and requirements.
Universal SASE includes a high-performance and scalable Cloud network, and best-in- class components such as Security Service Edge (SSE), Universal ZTNA, a Unified agent, Secure SD-WAN and Digital Experience Monitoring. Fortinet Universal SASE ensures the utmost security for all users everywhere, whether they are accessing the web, corporate applications, or SaaS applications.
Secure Access to Any Application With SASE
Fortinet SASE provides secure internet access, secure corporate access, and secure SaaS access for comprehensive security in a single solution. Secure web gateway (SWG), zero-trust network access (ZTNA), cloud access security broker (CASB), Firewall-as-a-Service (FWaaS), secure SD-WAN, and digital experience monitoring (DEM) all run on one OS with one agent, and can be managed with a single console.
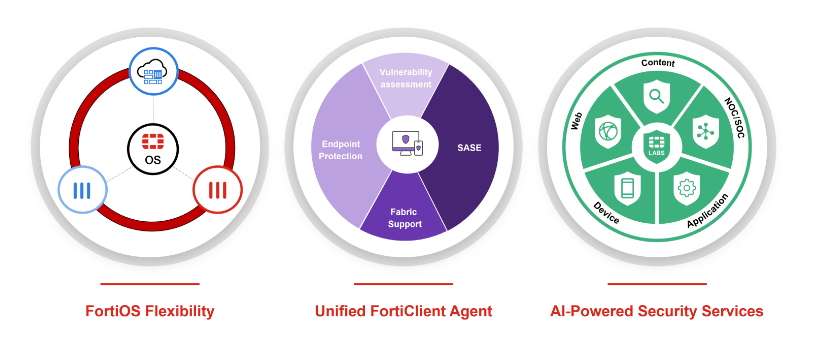
Powerful and Flexible Security Enforcement
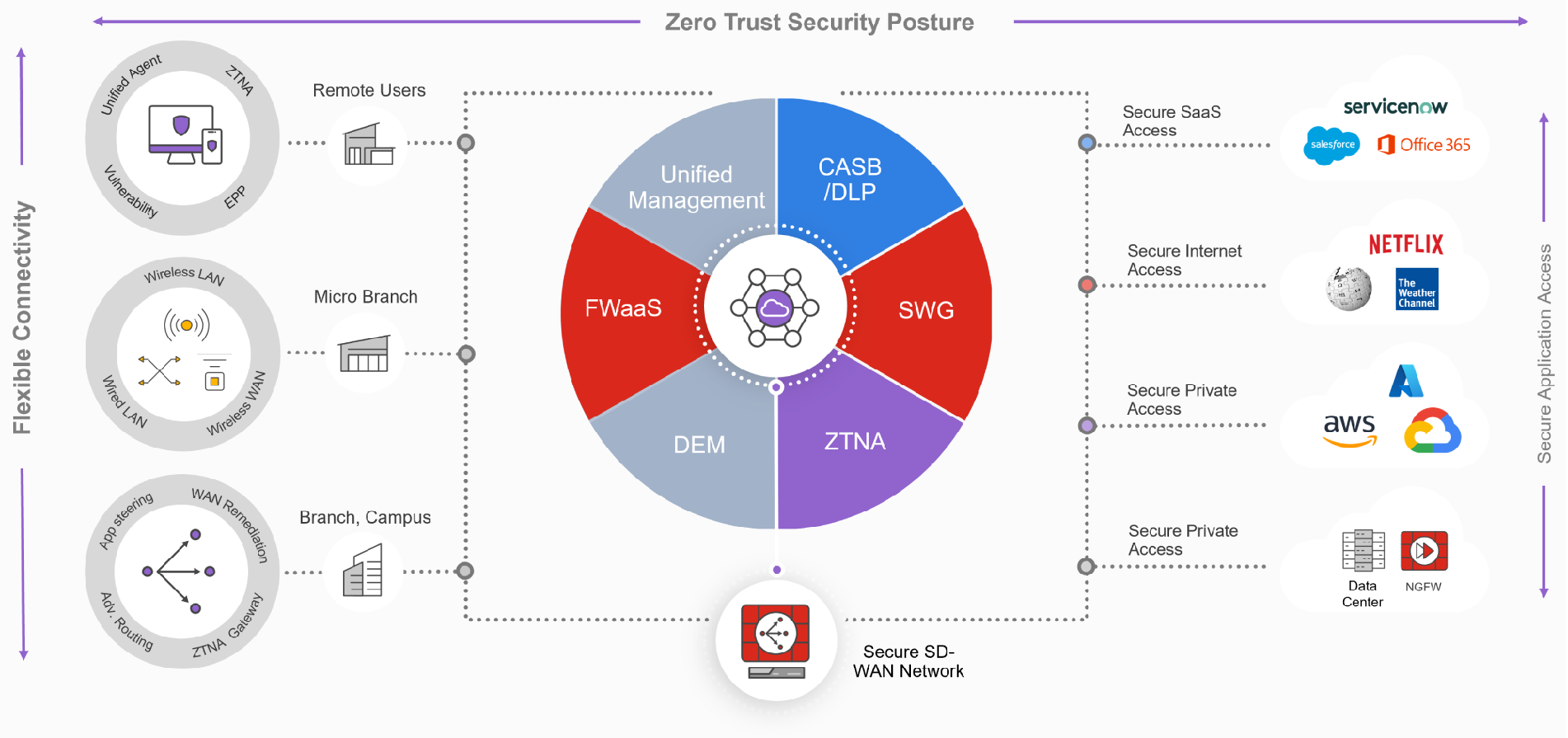
Our unique secure networking strategy is driven by a single operating system (FortiOS) and enhanced with FortiGuard AI-Powered Security Services. Our innovative approach weaves security and networking functionality into a single, integrated system to deliver consistent security and user experience to any user in any location. FortiSASE enables organizations to secure access to the web, cloud, and applications with enterprise-grade cybersecurity, a unified agent, and superior user experience.
Comprehensive Control, Visibility, and Analytics
Our intuitive user interface includes unified network and security visibility and is easy to configure. You can instantly see endpoints, users, point-of-presence graphical information, and threat analytics. Also, FortiAnalyzer, in conjunction with FortiSASE, provides centralized logging and response capabilities for networking and security across the entire organization. This enables organizations to understand their network and security events, facilitating effective incident response and mitigation.
Watch the Video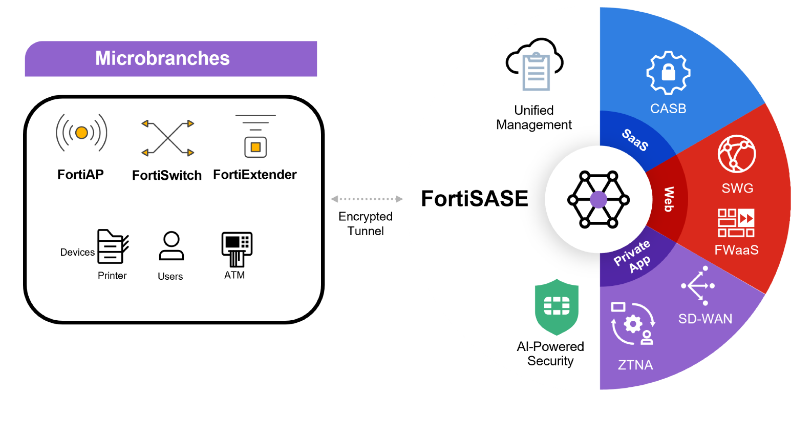
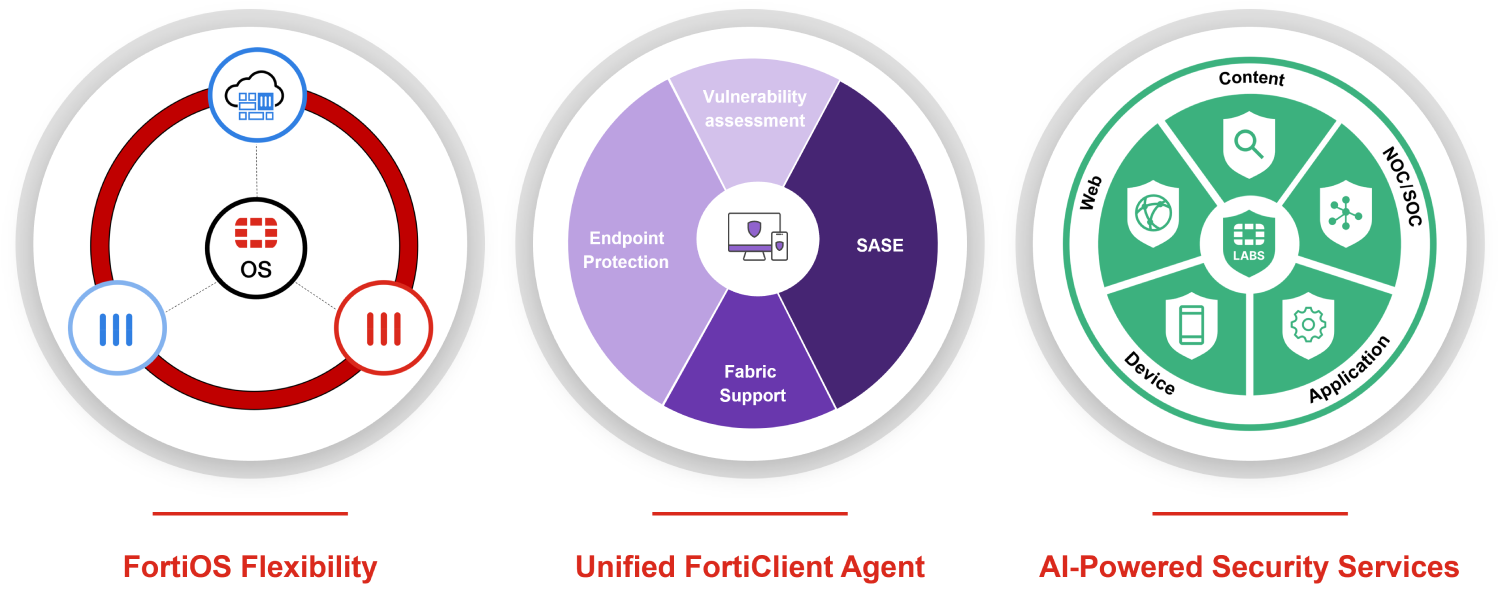
Microbranch Security, a Unique Capability
FortiSASE includes expanded integrations with the Fortinet WLAN/LAN and FortiExtender portfolios to support organizations securing microbranches and related devices. Our access points and extenders intelligently offload traffic to a SASE location for comprehensive security inspection at scale, for all devices. You can take a new approach to cloud-based security by extending enterprise-grade protection to microbranches without additional appliances, agents, or services.
Watch Demo of FortiExtender and SASE IntegrationFeatures and Benefits
UNIFIED FORTICLIENT AGENT
Both secure access and endpoint protection with a single, unified agent
FULL VISIBILITY/EASY MANAGEMENT
Single management console with DEM for simple and efficient operations
CONSISTENT SECURITY EVERYWHERE
Consistent protection for on-prem & remote users to reduce gaps and configuration overhead
SHADOW IT PREVENTION
SaaS application monitoring, risk assessment, and policy enforcement with dual-mode CASB
GLOBAL COVERAGE AND SCALABILITY
High-performance and scalable cloud network with 100+ locations globally
AUTHENTICATION AND CONTROL
Consistent application access control in all locations with Universal ZTNA
FortiSASE Use Cases
Secure Internet Access
Cloud-based firewall and secure proxy to enable anytime, anywhere security when browsing the web
Secure Private Access
Flexible and granular secure connectivity to corporate applications with integration of Fortinet Secure SD-WAN and ZTNA solution
Secure SAAS Access
Granular control over secure access to SaaS applications with inline and API-based cloud security broker (CASB)
Enterprise Analyst Recognition
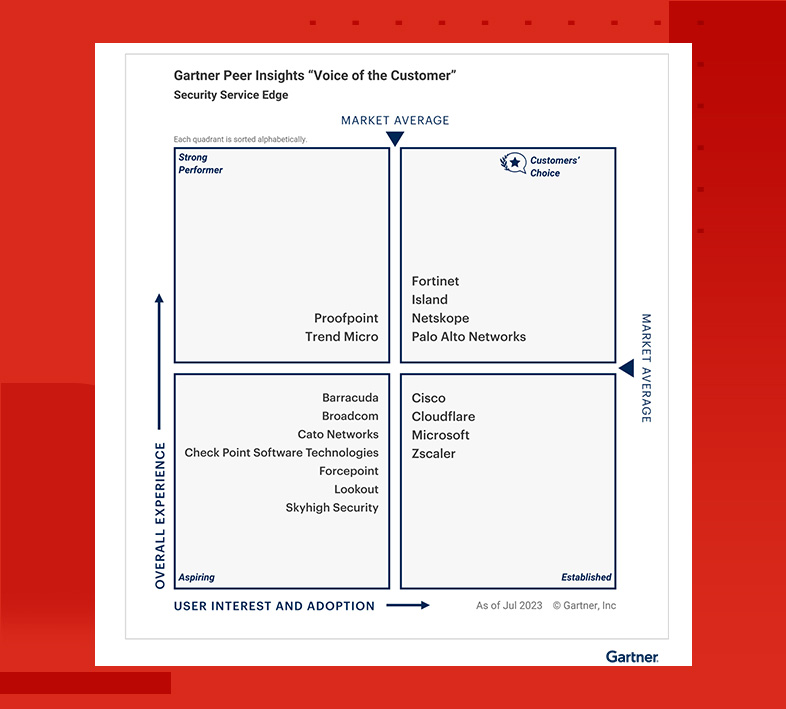
Fortinet is recognized as a Gartner® Peer Insights™ Customers' Choice for Security Service Edge (SSE)
Fortinet is not only recognized as a Customers’ Choice in the Voice of the Customer for Security Service Edge, but 96% of respondents are willing to recommend with a 4.7 out of five overall rating based on 84 reviews as of Jul’23.
Gartner® Peer Insights™ is a public platform that offers verified, first-hand reviews of enterprise software and services from experienced IT professionals.
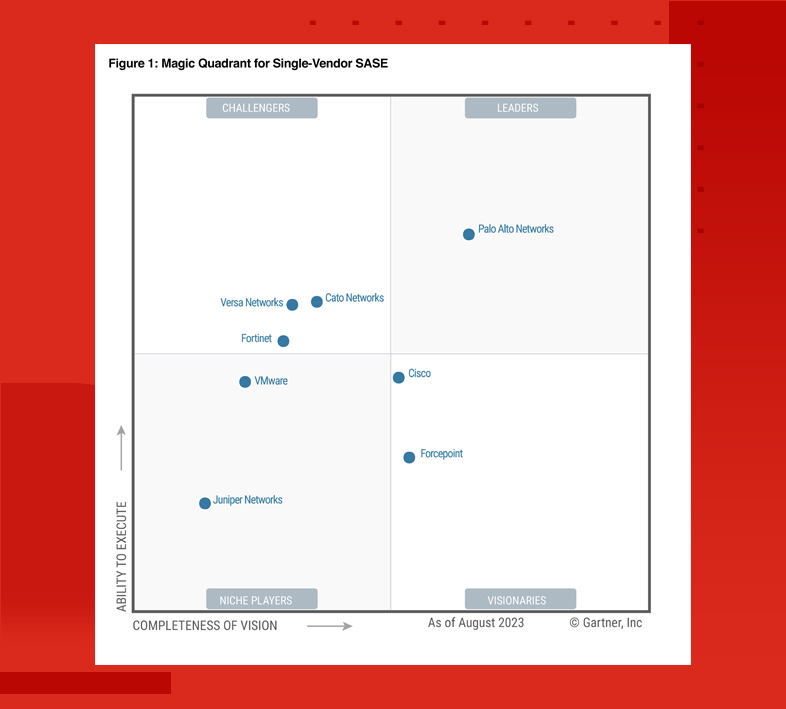
Fortinet Named a Challenger in the 2023 Gartner® Magic Quadrant™ for Single-Vendor SASE
Fortinet delivers unified management using a single console while delivering seamless integration of SD-WAN and cloud-delivered AI-powered security to secure the hybrid workforce.
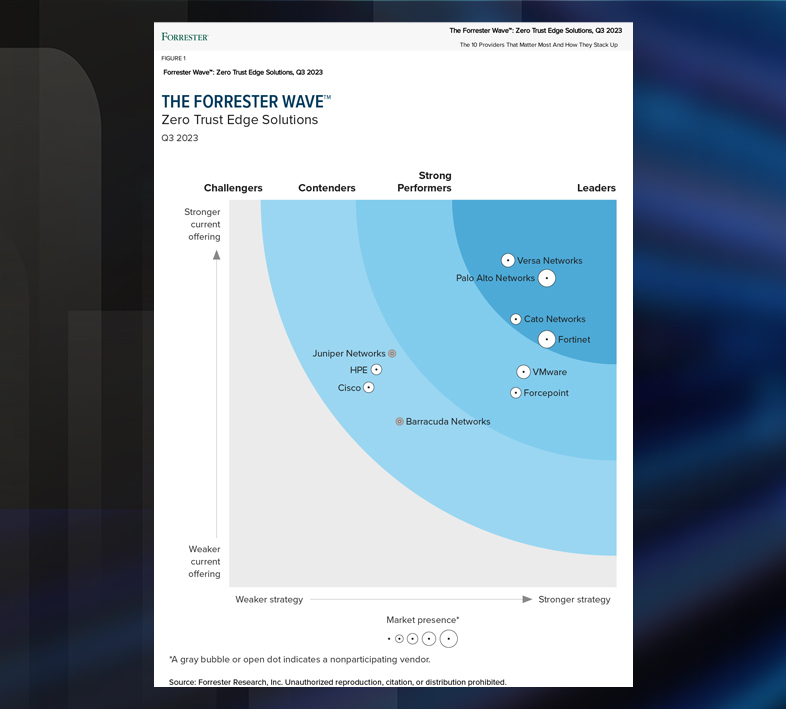
Fortinet Named a Leader in The Forrester Wave™: Zero Trust Edge Solutions, Q3 2023
FortiSASE delivers industry-leading value, securing users on and off the network with a unified end-user agent that provides both endpoint security and Zero Trust Edge innovations.
FortiGuard AI-Powered Security Services
FortiGuard Labs, Fortinet’s cybersecurity threat intelligence and research organization is comprised of experienced threat hunters, researchers, analysts, engineers, and data scientists. This elite team develops and enhances FortiGuard AI-powered Security Services including inline malware prevention, IPS, and DLP. FortiGuard Labs also provides valuable expert help through FortiGuard Expert-driven Security Services.
Content Security:

FortiGuard Antivirus Services
Protects against the latest polymorphic attacks, viruses, malware (including ransomware), and other threats.

FortiGuard Data Loss Prevention Service
Blocks intentional and accidental disclosures of sensitive data while addressing key requirements for data security associated with major frameworks.

FortiGuard AI-Based Inline Malware Prevention Service
Performs AI-powered real-time inspection of files for protection against unknown threats, zero-days, and sophisticated file-based attacks.
Web Security:

FortiGuard DNS Security Services
Provides full visibility into DNS traffic while blocking high-risk domains including malicious newly registered domains (NRDs) and parked domains.

FortiGuard URL Filtering Service
Uses AI-powered behavior analysis and correlation to block unknown malicious URLs almost immediately, with near-zero false negatives.

FortiGuard Anti-Bonet and C2 Service
Blocks unauthorized attempts to communicate with compromised remote servers for both receiving malicious commands and extracting information.
Device Security:

FortiGuard IPS Services
Utilizes the latest threat intelligence to perform deep packet inspection/SSL inspection of network traffic to detect and block malicious traffic and activities.

FortiGuard OT Security Service
Extends IPS protections to identify and police most of the common ICS/OT/SCADA protocols to detect and block exploits targeting OT vulnerabilities.

FortiGuard Anti-Bonet and C2 Service
Blocks unauthorized attempts to communicate with compromised remote servers for both receiving malicious commands and extracting information.
Application Security:

FortiGuard CASB Services
Provides a dual-mode (inline and API-based) cloud access security broker (CASB) solution for securing applications, monitoring their usage, and safeguarding related data.

FortiGuard AntiSpam Service
Dramatically reduces spam at the perimeter through a multi-layered approach to filtering unwanted and malicious email.
SOC NOC Security:

FortiGuard Attack Surface Security Service
Assesses and rates your Security Fabric infrastructure and controls against best practices and major security and compliance frameworks. Includes coverage for connected IoT devices.
FortiCare Support & Professional Services
Fortinet is dedicated to helping our customers succeed, and every year FortiCare services help thousands of organizations get the most from their investments in Fortinet's products and services. To achieve this, FortiCare follows the life-cycle approach and provides unique services to help our customers in their success journeys. For ease of purchasing, FortiSASE includes FortiCare Premium services.

Technical Support Services
Various per-device options are available for efficient operations. FortiCare Elite option provides a 15-minute response time for critical products.